What is Multi-Factor Authentication (MFA)?
Multi-factor authentication is the process by which a user is required to provide two or more verification factors so they can obtain access to online resources such as accounts, portals, applications. These verification factors need to be from independent source/s – for example a third party app, via SMS or email – to ensure the necessary level of protection.
It is also known as two-factor authentication (2FA), however – as the name suggests – 2FA only uses two of the available additional sources to verify the identity of the user, whereas MFA uses two or more.
MFA is considered to be a core component of a strong Identity and Access Management (IAM) policy, as it decreases the likelihood that you or your organisation will be the victim of a successful cyber attack.
Our research shows that simply adding a recovery phone number to your Google Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks …
Source: Google
Who should be using MFA? And why is it important for businesses?
Both individuals and businesses should be using multi-factor authentication across personal and company devices to ensure best practice digital security measures. However, according to Alexander Weinart, Director of Identity Security at Microsoft, enterprise cloud users have only an 11% adoption rate of MFA within their organisation.
In addition, with the increase in remote working during the events of Covid-19 – and with many companies choosing to continue this remote working structure where possible – there has been an increase in the number of devices that access an organisation’s network. This in turn provides greater opportunity for businesses to fall prey to digital threats, which may be prevented through security programs like MFA.
If your organisation does not yet have MFA as a mandatory requirement, it is recommended you take the initiative and implement it across your own devices to ensure your accounts are less likely to be compromised.
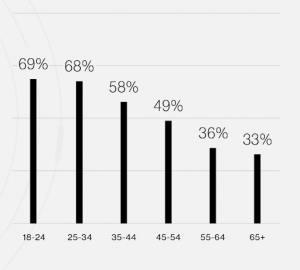
2-factor authentication adoption by age
Source: DUO Security
The three types of Multi-Factor Authentication
There are three main types of MFA, and they can be categorised in the following way:
- Knowledge
- Possession
- Inherence
Knowledge
This type of MFA refers to something that you know, which could be a password or a pin. This type is also commonly used in ‘Multi-step authentication (MSA)’, which is when you have to complete a secondary step within a platform to gain access to the account. The most common use of this would be
Step 1) password
Step 2) security question, e.g. mother’s maiden name.
MSA is often confused with MFA, however the key difference is that MSA does not have an independent, third-party source involved, whereas MFA could.
For an MFA requiring knowledge, anything that you can remember and then type/do/say will fall into this category, from passwords and combinations to PINs or code words.
Possession
The ‘possession’ type of MFA refers to something you are able to physically access, such as a safety token or even a physical key. This token could be:
- a one-time password (OTP) generated by a smartphone app like DUO
- a OTP sent via email or SMS
- a USB dongle with an encrypted ‘key’
- and more.
These MFAs are highly secure due to the requirement for the user to have access to more than just information, for example having the device to access the smartphone app, or having the email access for a OTP sent via email.
Mobile push notifications are the most common authentication method, used by 68% of MFA users
Source: DUO Security
Inherence
Inherence in MFA refers to ‘something you are’, which includes any part of your body that can be used for verification. This type of verification is generally only possible through the use of biometric detection, for example fingerprint scanning, retina scanning, facial recognition, etc.
With smartphones increasing their capabilities in the field of inherence exponentially over the past five years, this type of MFA will likely continue to grow in popularity. One day it may even be that MFAs can use voice detection passwords and determine via voice stresses and nuances if a user is under duress when attempting to access a device. While this level of analysis is not yet at a stage of accuracy for development, it’s an interesting look into where the future of inherence MFA could be heading thanks to the increasingly sophisticated capabilities of voice detection software.
77% of mobile devices have biometric security enabled.
Source: DUO Security
What are the benefits of MFA?
There are a number of benefits to using MFA at both the individual and business level. These include:
Improved cyber security
Weak or stolen credentials, such as those used in single-factor authentication, are used in 95% of all Web application attacks, according to the 2020 Verizon Data Breach Investigations Report. Multi-factor authentication is a highly effective security measure to prevent an individual or organisation’s confidential data from being compromised through a phishing attack or data breach.
This in turn can also improve consumer trust in an organisation that has mandatory MFA protocols in place, as it assures consumers that the company is less likely to experience a data breach which could put their confidential information at risk.
Another consequence of improved cyber security for a business can be reduced cost, as while the use of a third party MFA service for enterprises may incur a service or platform charge (dependent on the third party), the cost of this is much lower than the cost a data breach would generate to the business, both financially and in relation to market share, brand reputation and consumer trust.
Streamlined access
Due to the ongoing complexity of IT network changes, advancements in remote access, the increase in remote workforces etc, MFA has made it possible to ensure users can access their devices/accounts/organisation’s network in a more streamlined way without compromising the security of the device they’re accessing.
For example, if a user is logging into their work email from a trusted device from which they have logged in before, for example their personal smartphone, they will not necessarily be prompted for a OTP in order to authenticate every login. The exceptions to this are if the setting on their account is to prompt for a OTP each time you access regardless of the device having accessed the account in the past, or if you have a finite time period in which streamlined access will be granted, eg a OTP is required once a month.
Increased employee flexibility and productivity
This benefit ties a little into both improved security and streamlined access, however is deserving of its own point. It can be difficult for employees to remember passwords, particularly passwords that are made up of random sequences of letters, numbers and special characters. Consequently, many employees choose more simple passwords that are thus also more easily breached by attackers, or are consistently forgetting their password and having to go through the reset password process on a regular basis, making them frustrated when attempting to access accounts or portals.
MFA allows employees the flexibility to have passwords that are easily fillable through third party apps or OTPs, which in turn increases productivity and improves employee sentiment.
What is the future of MFA?
In the future, it is expected that the most prevalent type of MFA used by organisations as well as individuals will be the current subset known as ‘adaptive authentication’ or ‘risk-based authentication’. This type of MFA analyses factors outside of the three categories of knowledge, possession and inherence, including context and behaviour.
For example, the MFA might take the following into consideration:
- From where is the user trying to access the information? (using geo-targeting)
- When is the user trying to access the information? (using behavioural working hours)
- What is the device being used? (using previous login history)
- What type of connection is being used, private or public? (risk assessment)
Based on the answers the program determines to questions like these, the adaptive authentication service will choose to allow the user to proceed or not based on their risk assessment.
This type of MFA is tailored to the organisation choosing to use it, and as such is a strong front-line of defence against cyber attacks.
Does your business have MFA?
If your business does not yet have MFA included as part of your cyber security policy, we can help. Our team at Kloud IT can help you develop and implement a security policy that ensures multi-factor authentication is a core part of your first line defence against digital threats.
Contact us today to discuss how we can help your business.



